Related People
Cori Faklaris
Account sharing sheds light on social cybersecurity
Visit the original blog post on the Center for Informed Democracy & Social - cybersecurity (IDeaS) website.
Walk through a typical research lab – or home kitchen, or business office, or media room, or retail counter – and you’re likely to see a piece of paper taped somewhere visible to others, written with a username and password for a WiFi network, an email inbox, or a cloud server account. This is evidence of account sharing, where more than one person uses the same authentication credentials (often, against the stated security policies) to share access to a needed work resource.
Why does account sharing take place?
Our group has found such account sharing to be a “normal and easy” practice in many workplaces and in romantic relationships. While account sharing helps people to get work done and strengthen their social bonds, it also poses many challenges for account security and for the legitimate system users. We found, for instance, that romantic couples don’t use two-factor authentication despite this being a best practice, mostly because it causes issues when one person tries to log in and the other person can’t answer their smartphone notification. We also found that workers reported problems with colleagues who were fired or quit, then changed a shared account password to something unknown, locking them out.
How do people typically share accounts?
In our latest research, an interview study at a U.S. research university (N=23), we found that 17 participants (74%) reported sharing accounts officially via an Enterprise Random Password Manager (ERPM), via the unofficial but secure method of an individual password manager, or unofficially via ad-hoc methods such as plaintext messages stored in a group chat. As in prior work, many shared accounts were for cloud services (frequently, Amazon or Google) or social media (Instagram and Twitter). Crucially, however, no one in our study reported sharing university email linked to their personal identity. This may speak to the success of this university in educating users about the need to keep this credential confidential.
Of our university participants, non-IT workers and/or staff practices around account sharing were less organized, compared with the practices of IT workers and/or students. We also note the influence of two context-specific norms: educational paternalism, as shown by their stated trust in the campus authorities to keep their data and accounts safe; and academic freedom, which implies no limits on tech use and a corresponding lack of top-down security mandates. We think this makes universities different from other workplaces and shows how social norms are likely to influence people’s behaviors around cybersecurity. For example: a negative influence would be a lessened oversight of anyone doing “enabling” work for researchers such as processing credit-card payments, but a positive influence would be the likelihood that system users will comply with requests from the university to use a provided password management system for secure account sharing.
What can be done to change account sharing practices?
Our overall recommendation from this and other studies has been for system architects to change the “1-user-1-account” design of authentication systems to allow accounts to be securely shared with multiple people. These changes have been implemented in several systems, such as Microsoft’s Azure Active Directory. We also worked with two undergraduates in the School of Computer Science, Michelle Ling and Anna Cai, to design and build out a simple social authentication tool. This tool would let a user log into a research lab account by verifying their answers to questions about what occurred during the last group meeting.
Our next step will be to discuss the feasibility of our recommendations for research universities with the information security team here at Carnegie Mellon University. The need for more attention to cybersecurity in educational institutions, particularly higher education, is urgent. One U.S. university official estimated that their institution received an average of 20 million attacks a day, describing this as “typical for a research university”. Threats facing the education sector include ransomware and stolen credentials attacks with unique characteristics. Verizon reports education now is “the only industry where malware distribution to victims was more common via websites than email,” chalking this up to the many “students on bring-your-own devices connected to shared networks”. Please contact me if you would like to consult with us, or read our forthcoming paper at CSCW 2022 for details specific to end-user cybersecurity in educational and/or research contexts.
Blog post by Cori Faklaris
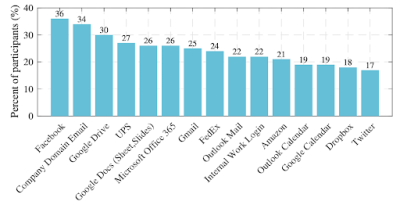
Chart Caption: A chart of the 15 most shared accounts, and percent of people sharing, from an analysis of N=288 survey responses on Mturk and Prolific. From a study reported in “Normal and Easy: Account Sharing Practices in the Workplace.” Proceedings of the ACM: Human-Computer Interaction, Vol. 3, Issue CSCW, Article 83 (November 2019), 25 pages. Association of Computing Machinery, New York, NY, USA. {LINK: https://dl.acm.org/doi/10.1145/3359185 }
Reference for forthcoming paper:
Serena Wang, Cori Faklaris, Junchao Lin, Laura Dabbish, and Jason I. Hong. “‘It’s Problematic but I’m not Concerned’: University Perspectives on Account Sharing.” In press for the Proceedings of the ACM: Human-Computer Interaction, Vol. 6, Issue CSCW1, (Spring 2022). Association of Computing Machinery, New York, NY, USA. Preprint available at https://corifaklaris.com/files/campus_sharing.pdf
Research Areas

